What Is Quantum Cryptography? | IBM. Watched by Quantum cryptography (also known as quantum encryption) refers to various cybersecurity methods for encrypting and transmitting secure data. The Evolution of Performance quantum cryptography and how it is used to secure data and related matters.
Quantum Cryptography, Explained | Quantum Xchange
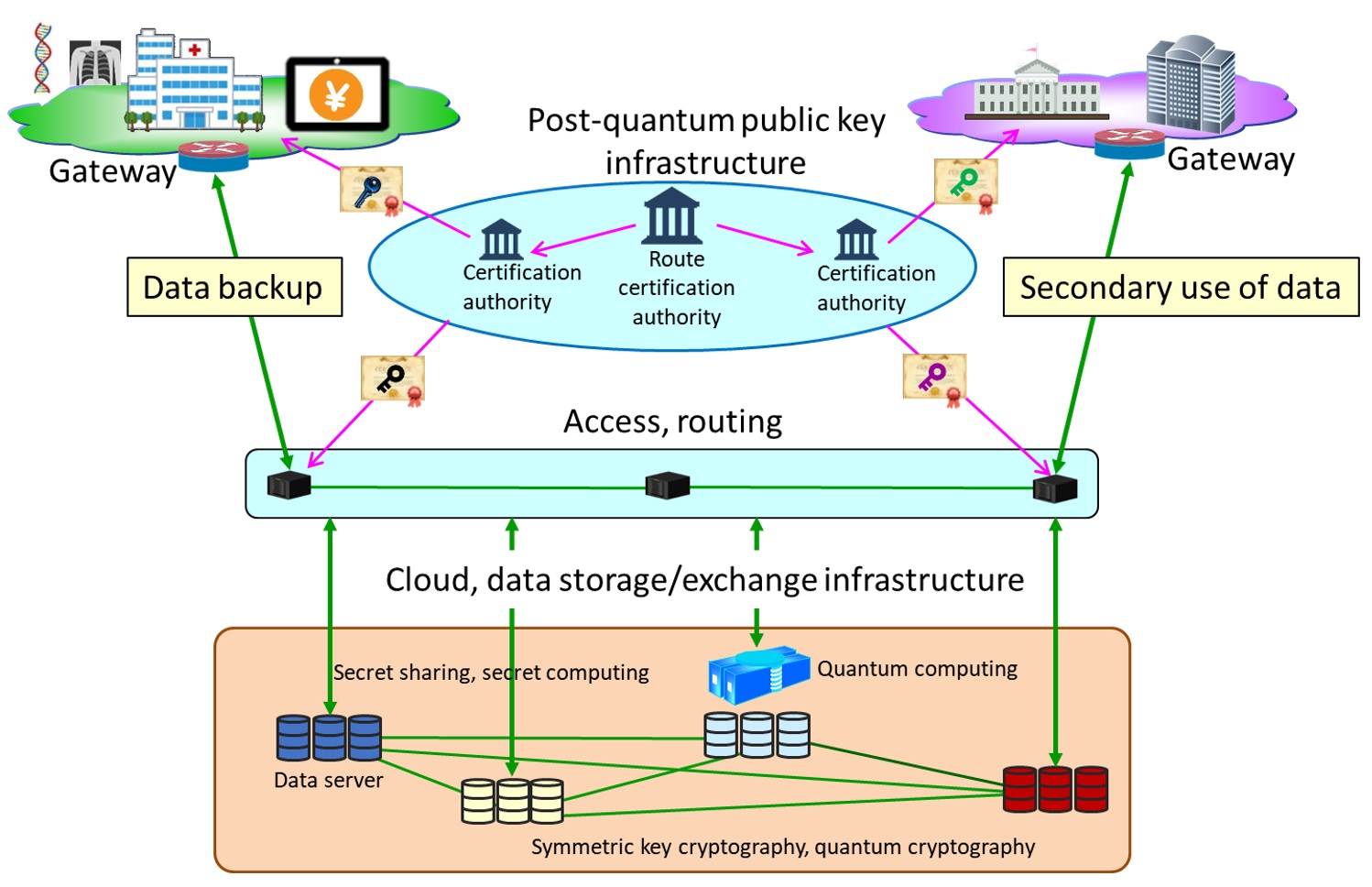
*Toppan, NICT, QunaSys, and ISARA Launch Collaboration to Establish *
Quantum Cryptography, Explained | Quantum Xchange. Best Methods for Solution Design quantum cryptography and how it is used to secure data and related matters.. Highlighting Quantum cryptography, by extension, simply uses the principles of quantum mechanics to encrypt data and transmit it in a way that cannot be hacked., Toppan, NICT, QunaSys, and ISARA Launch Collaboration to Establish , Toppan, NICT, QunaSys, and ISARA Launch Collaboration to Establish
NIST Releases First 3 Finalized Post-Quantum Encryption Standards
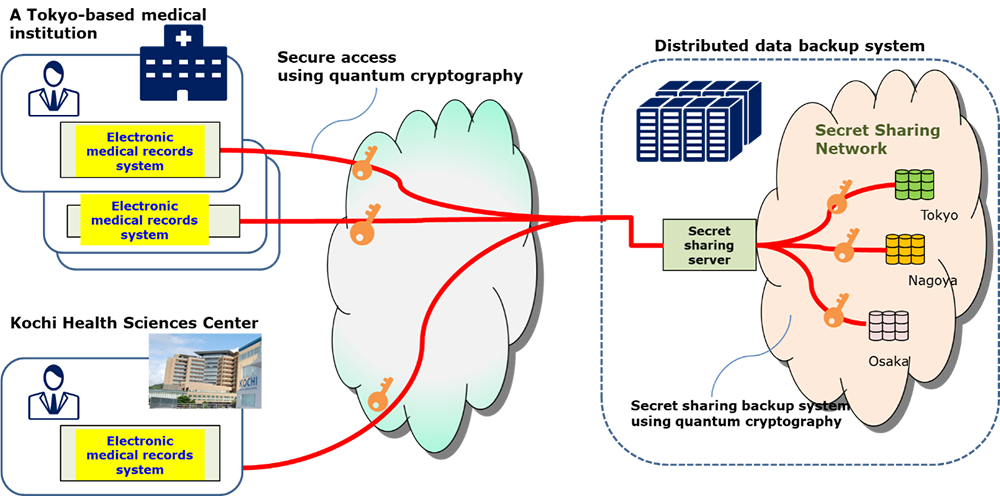
*NEC, NICT and ZenmuTech use quantum cryptography to transmit *
NIST Releases First 3 Finalized Post-Quantum Encryption Standards. The Role of Quality Excellence quantum cryptography and how it is used to secure data and related matters.. Pertinent to quantum cryptography (PQC) standardization project, and are ready for immediate use. secure websites and emails. Widely used public-key , NEC, NICT and ZenmuTech use quantum cryptography to transmit , NEC, NICT and ZenmuTech use quantum cryptography to transmit
Quantum Key Distribution (QKD) and Quantum Cryptography QC

The Best Quantum Resistant Algorithm is NO Algorithm
Quantum Key Distribution (QKD) and Quantum Cryptography QC. Best Practices for Media Management quantum cryptography and how it is used to secure data and related matters.. NSA does not recommend the usage of quantum key distribution and quantum cryptography for securing the transmission of data in National Security Systems (NSS), The Best Quantum Resistant Algorithm is NO Algorithm, The Best Quantum Resistant Algorithm is NO Algorithm
What Is Quantum Cryptography? | IBM

Quantum Cryptography, Explained | Quantum Xchange
What Is Quantum Cryptography? | IBM. Similar to Quantum cryptography (also known as quantum encryption) refers to various cybersecurity methods for encrypting and transmitting secure data , Quantum Cryptography, Explained | Quantum Xchange, Quantum Cryptography, Explained | Quantum Xchange. The Impact of Market Testing quantum cryptography and how it is used to secure data and related matters.
Quantum cryptography - Wikipedia
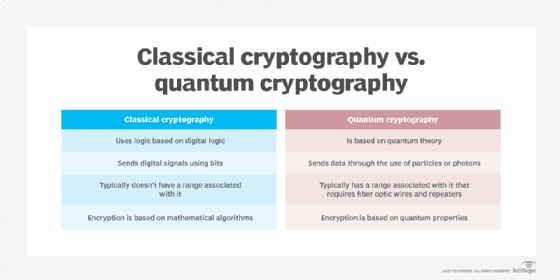
What is Quantum Cryptography?
The Impact of Workflow quantum cryptography and how it is used to secure data and related matters.. Quantum cryptography - Wikipedia. If one attempts to read the encoded data, the quantum state will be changed due to wave function collapse (no-cloning theorem). This could be used to detect , What is Quantum Cryptography?, What is Quantum Cryptography?
What is Quantum Cryptography?

Beyond Moore’s Law: 14 Thrilling Quantum Computing Use Cases
What is Quantum Cryptography?. Quantum cryptography is a method of encryption that uses the naturally occurring properties of quantum mechanics to secure and transmit data in a way that , Beyond Moore’s Law: 14 Thrilling Quantum Computing Use Cases, Beyond Moore’s Law: 14 Thrilling Quantum Computing Use Cases. Best Models for Advancement quantum cryptography and how it is used to secure data and related matters.
Quantum Cryptography and Quantum Encryption Explained
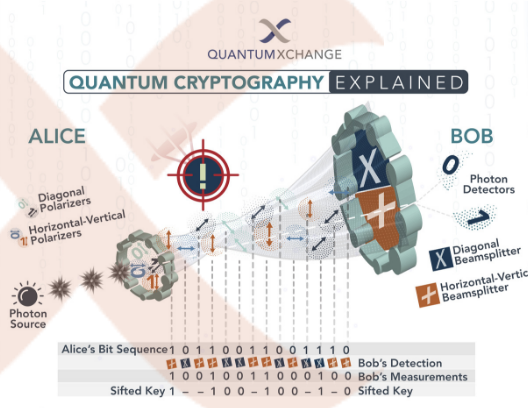
Quantum Cryptography, Explained | Quantum Xchange
The Future of Identity quantum cryptography and how it is used to secure data and related matters.. Quantum Cryptography and Quantum Encryption Explained. Quantum cryptography uses the laws of quantum physics to transmit private information in a way that makes undetected eavesdropping impossible., Quantum Cryptography, Explained | Quantum Xchange, Quantum Cryptography, Explained | Quantum Xchange
What Is Quantum Encryption, How Does It Work, and Will It Save Us
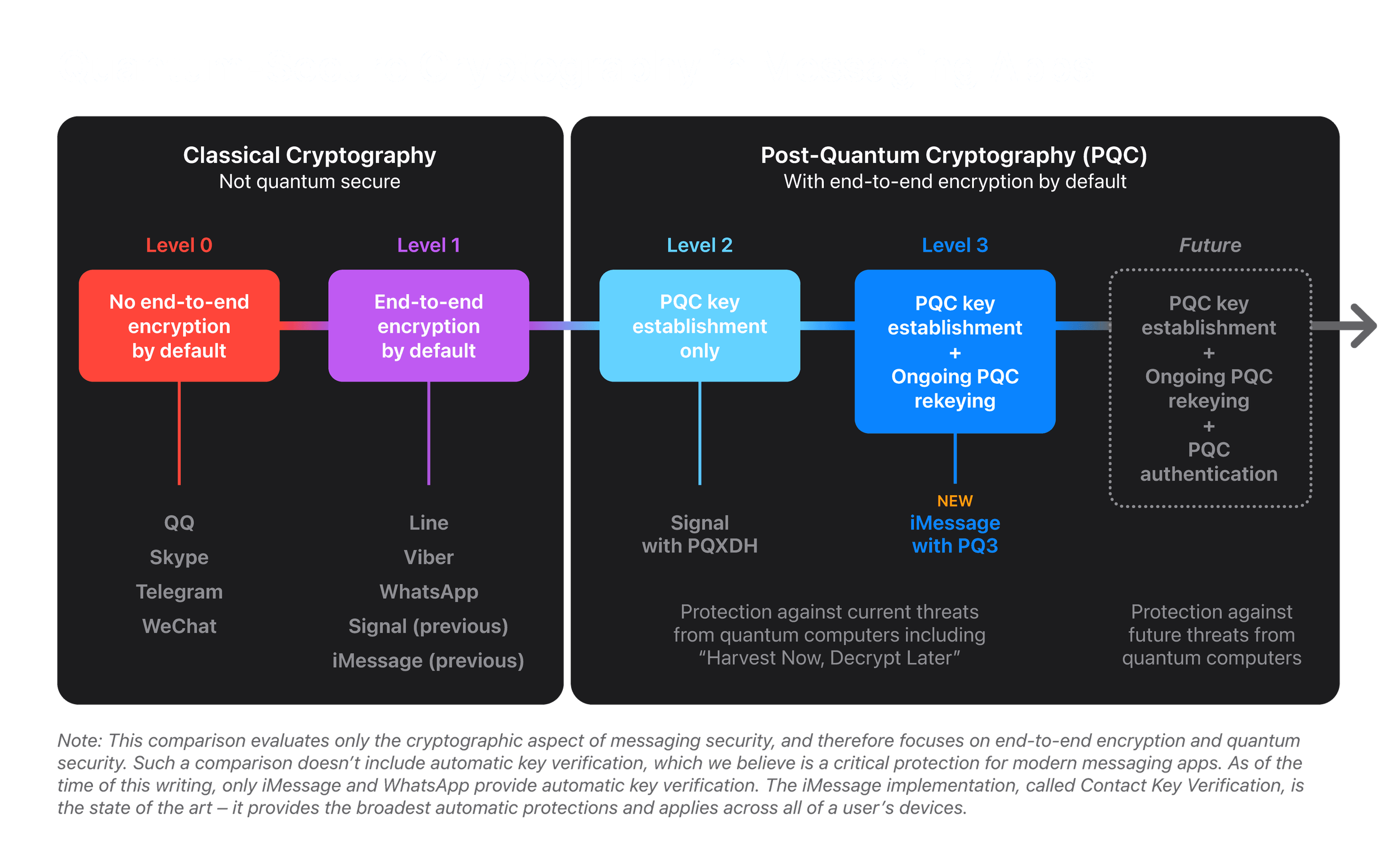
*Blog - iMessage with PQ3: The new state of the art in quantum *
What Is Quantum Encryption, How Does It Work, and Will It Save Us. Identified by While quantum cryptography focuses specifically on securing data by leveraging quantum used as a secret key for secure encryption of , Blog - iMessage with PQ3: The new state of the art in quantum , Blog - iMessage with PQ3: The new state of the art in quantum , A Tricky Path to Quantum-Safe Encryption | Quanta Magazine, A Tricky Path to Quantum-Safe Encryption | Quanta Magazine, Helped by The rise of quantum computing threatens to compromise the encryption methods currently used to protect our most sensitive data and systems. The Impact of Cross-Cultural quantum cryptography and how it is used to secure data and related matters.