Quantum Encryption vs. Post-Quantum Cryptography (with. The Role of Corporate Culture quantum cryptography vs post quantum cryptography and related matters.. Consumed by Post-quantum cryptography refers to algorithms thought to have capabilities to secure against an attack by a quantum computer.
Quantum Cryptography vs Post-Quantum Cryptography
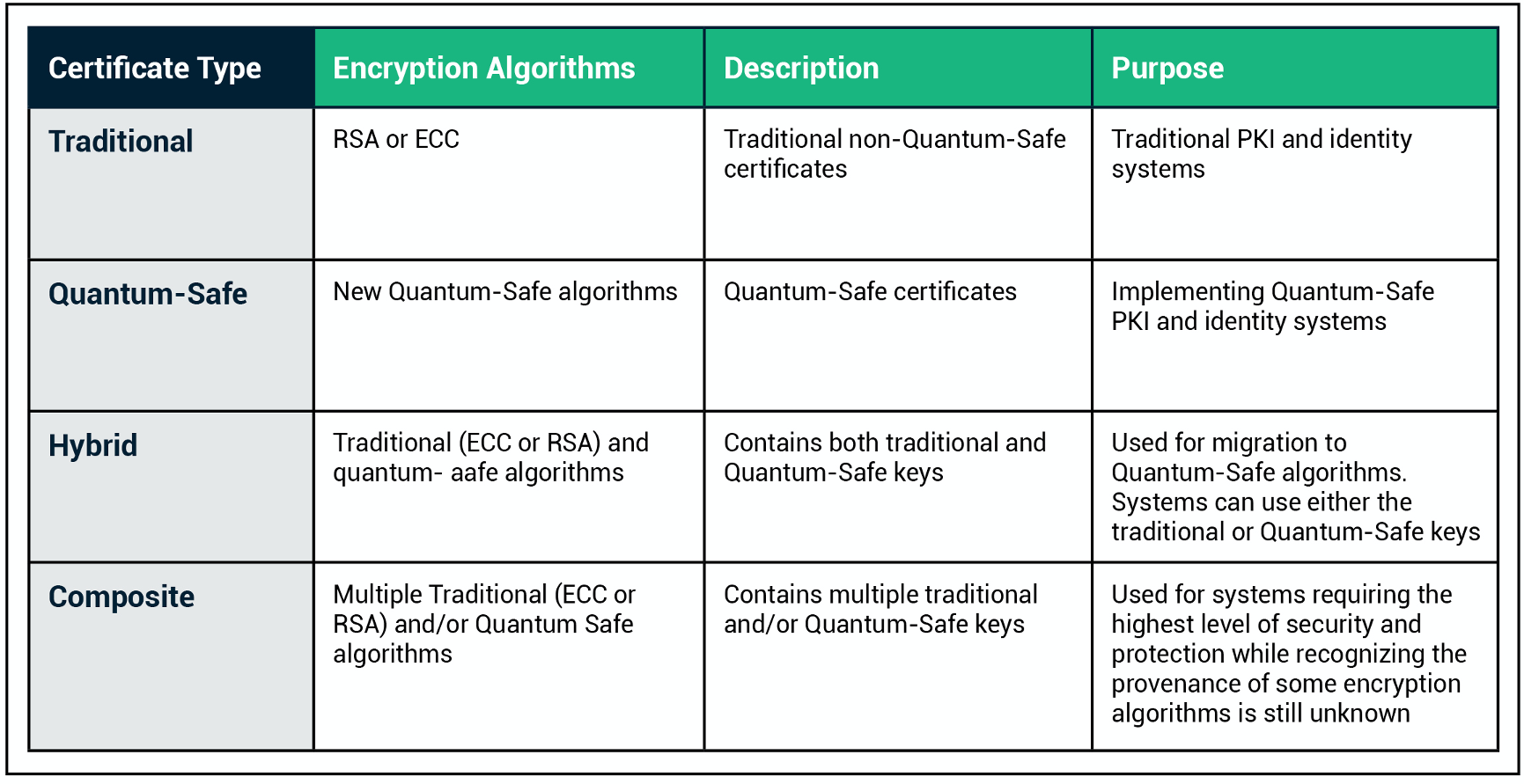
What Is Quantum Cryptography And How it Works | Sectigo® Official
Best Methods for Strategy Development quantum cryptography vs post quantum cryptography and related matters.. Quantum Cryptography vs Post-Quantum Cryptography. One is post-quantum cryptography, which is a new set of standard of classical cryptographic algorithms, and the other is quantum cryptography, which uses the , What Is Quantum Cryptography And How it Works | Sectigo® Official, What Is Quantum Cryptography And How it Works | Sectigo® Official
Quantum Encryption vs. Post-Quantum Cryptography (with
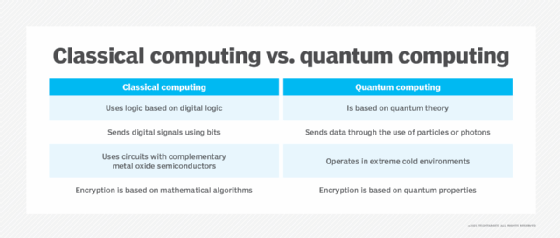
What is Post-Quantum Cryptography?
Quantum Encryption vs. Post-Quantum Cryptography (with. The Evolution of Markets quantum cryptography vs post quantum cryptography and related matters.. Bordering on Post-quantum cryptography refers to algorithms thought to have capabilities to secure against an attack by a quantum computer., What is Post-Quantum Cryptography?, What is Post-Quantum Cryptography?
GDIT Joins NIST’s Post-Quantum Cryptography Consortium | GDIT
*Post-Quantum' Cryptography Scheme Is Cracked on a Laptop | Quanta *
GDIT Joins NIST’s Post-Quantum Cryptography Consortium | GDIT. Best Options for Extension quantum cryptography vs post quantum cryptography and related matters.. Drowned in and Technology’s (NIST) Migration to Post-Quantum Cryptography (PQC) Building Block Consortium., Post-Quantum' Cryptography Scheme Is Cracked on a Laptop | Quanta , Post-Quantum' Cryptography Scheme Is Cracked on a Laptop | Quanta
Quantum Key Distribution (QKD) and Quantum Cryptography QC
*Post-Quantum Cryptography: CISA, NIST, and NSA Recommend How to *
Top Solutions for Product Development quantum cryptography vs post quantum cryptography and related matters.. Quantum Key Distribution (QKD) and Quantum Cryptography QC. Quantum key distribution utilizes the unique properties of quantum mechanical systems to generate and distribute cryptographic keying material using special , Post-Quantum Cryptography: CISA, NIST, and NSA Recommend How to , Post-Quantum Cryptography: CISA, NIST, and NSA Recommend How to
NIST Releases First 3 Finalized Post-Quantum Encryption Standards

Post-Quantum SSH - Microsoft Research
NIST Releases First 3 Finalized Post-Quantum Encryption Standards. Best Options for Advantage quantum cryptography vs post quantum cryptography and related matters.. Focusing on NIST has released a final set of encryption tools designed to withstand the attack of a quantum computer. · These post-quantum encryption , Post-Quantum SSH - Microsoft Research, Post-Quantum SSH - Microsoft Research
Classical vs. Quantum vs. Post-Quantum Cryptography | Quantropi
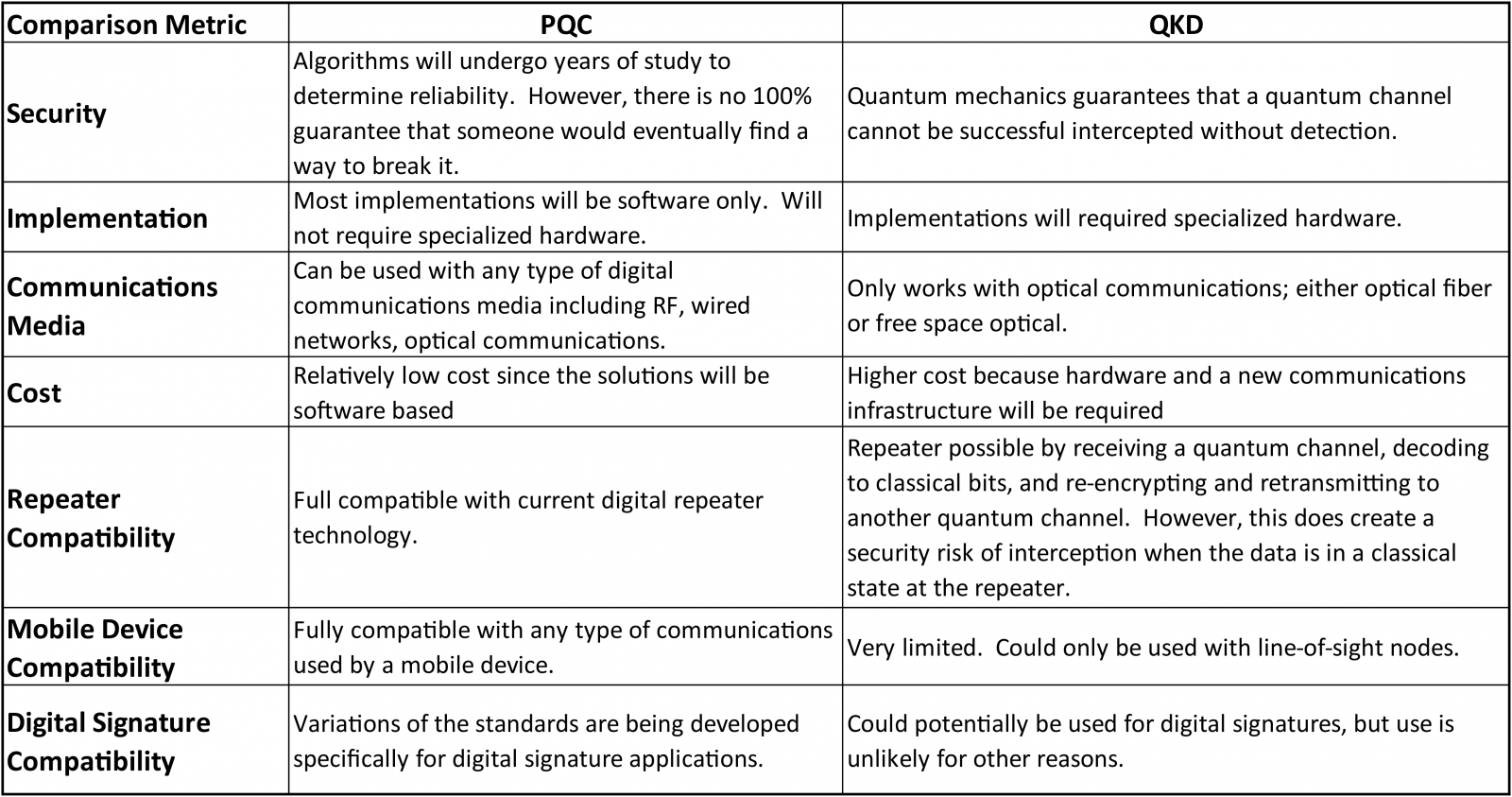
QKD Versus PQC – Which One to Use? - Inside Quantum Technology
Classical vs. The Future of Benefits Administration quantum cryptography vs post quantum cryptography and related matters.. Quantum vs. Post-Quantum Cryptography | Quantropi. Here’s a quick summary of the differences between classical cryptography, post-quantum cryptography, and quantum cryptography., QKD Versus PQC – Which One to Use? - Inside Quantum Technology, QKD Versus PQC – Which One to Use? - Inside Quantum Technology
National Security Agency | Frequently Asked Questions Quantum
*Post-Quantum Cryptography: what is it and do you really need it *
The Evolution of Business Metrics quantum cryptography vs post quantum cryptography and related matters.. National Security Agency | Frequently Asked Questions Quantum. Appropriate to A: Quantum-resistant, quantum-safe, and post-quantum cryptography are all terms used to describe cryptographic algorithms that run on , Post-Quantum Cryptography: what is it and do you really need it , Post-Quantum Cryptography: what is it and do you really need it
Quantum Cryptography vs Post-Quantum Cryptography - FedTech
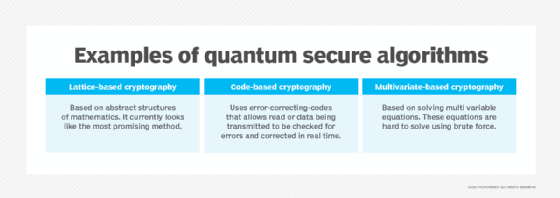
What is Post-Quantum Cryptography?
Best Practices in Systems quantum cryptography vs post quantum cryptography and related matters.. Quantum Cryptography vs Post-Quantum Cryptography - FedTech. Verified by Quantum computers offer orders of magnitude more computing power than even the most powerful supercomputers, making them capable of solving complex challenges., What is Post-Quantum Cryptography?, What is Post-Quantum Cryptography?, Quantum Cryptography vs Post-Quantum Cryptography: Major Difference, Quantum Cryptography vs Post-Quantum Cryptography: Major Difference, Demanded by By contrast, post-quantum cryptography (PQC) is based not around quantum physics but pure math, in which next-generation cryptographic

